Enhancing Your Computer Security: A Comprehensive Guide to Encryption & Tor
Unifying Cyber Security and Cryptocurrency: The Definitive Guide
The world of cryptocurrency, particularly Bitcoin, is a fascinating realm. Holding within its network confines billions of dollars worth of Bitcoins, it has become a tempting target for those with the technical prowess to crack into this digital treasure chest. But it's not as simple as one might think.
Bitcoin's robust network security is built on the backbone of a cryptographic hash function known as SHA256. SHA, an acronym that stands for Secure Hash Algorithm, provides military-grade encryption. This means that the odds of cracking a private key, essentially the password to access and transfer Bitcoins, are infinitesimally small—almost hitting rock-bottom at zero.
With such a formidable shield, breaches in Bitcoin's security generally do not occur within the protocol itself. Instead, they are often due to third-party lapses.
The Power Shift: From Banks to Individuals
In essence, Bitcoin and other cryptocurrencies have triggered a seismic shift in financial power dynamics. For centuries, financial institutions have held sway over our money, but now cryptocurrencies are ushering this power back into the hands of individuals. This is both empowering and daunting.
The Price of Financial Independence: Personal Responsibility
Being your own bank comes with an immense amount of personal responsibility. As you transition from traditional banking systems to cryptocurrency:
- You're compelled to stay aware and vigilant about your assets.
- You're personally accountable for protecting your own private keys.
- There are no banks or institutions to fall back on should things go awry.
“This power requires a high degree of personal responsibility and awareness.”
In sum, cryptocurrencies like Bitcoin arm you with unprecedented financial power. However, this power demands an elevated level of responsibility—to be cautious custodians of our own wealth in a digital realm.
Ensuring Optimal Security for Your Computer
In today's digital age, the security of your computer is paramount. Here's a step-by-step guide on how to make your computer ultra-secure:
Step 1: Eliminate Potential Threats
The first step in securing your computer involves eliminating potential threats. This includes removing software that may pose security risks. A prime example is the Windows operating system, often targeted by hackers worldwide due to its popularity.
Remember: “Prevention is better than cure.”
Step 2: Choose a Secure Operating System
After removing potential threats, it's time to replace them with more secure alternatives. Consider opting for an open-source operating system like Ubuntu. Being Linux-based and fully encrypted, Ubuntu offers robust security features that help protect your data.
- Why Ubuntu?: Open source: The code is publicly accessible, meaning it's constantly scrutinized and improved by the community.
- Fully encrypted: Your data is protected, making it difficult for unauthorized users to access.
Step 3: Anonymize Your Online Activities
The final step involves ensuring all your online activities are anonymous. This can be achieved with the help of an open-source program called Anonsurf.
By routing all network traffic through Tor (The Onion Router), Anonsurf anonymizes your whole computer. Whether you're using a browser, wallet or any other application connected to the internet, you remain completely hidden from potential intruders.
Remember: “Anonymity is a key aspect of privacy.”
This three-step process can significantly boost the security of your computer—making it resistant to most cyber threats out there. By adopting these measures, you transform your standard machine into an ultra-secure fortress that prioritizes privacy and data protection.
Why Linux is More Secure Than Other Operating Systems?
While many individuals may be more familiar with household names like Windows and Mac, Linux is actually the world's most popular choice for servers. In fact, a significant portion of the internet as we know it runs on Linux. But why is this the case? And what makes Linux seemingly more secure than its counterparts? While we won't delve too deeply into these questions, here are some key reasons why Linux stands out in terms of security:
1. Open Source Nature
First and foremost, one of the defining aspects of Linux is its open-source nature. This means that not only can anyone view the code that makes up the operating system, but it can also be maintained and improved upon by a large community of developers.
Remember: “Transparency promotes trust and improvement.”
This open-source model has several implications for security. With so many eyes examining the code, vulnerabilities are more likely to be spotted and fixed promptly. Additionally, this transparency provides assurance that there are no hidden backdoors within the system that could potentially compromise user data.
2. Complex Architecture
Unlike Windows, which has a relatively straightforward structure, Linux operates in many different environments and its architecture is much more complex. This complexity comes from its diverse range of consoles, packages, and multi-level component arrangements.
Did you know? “The complexity of an operating system can act as a barrier against viruses.”
This complexity makes it more difficult for viruses to access system files. In simpler terms, it’s like trying to find a specific room in a vast labyrinth—it's much harder to navigate than a single corridor.
3. Limited Administrator Rights
In many operating systems like Windows, users have administrator rights by default. This means they have access to everything in the system right from the get-go.
“Access rights can be both a privilege and a vulnerability.”
While this might seem convenient, it also means that if a virus manages to infiltrate the system, it can quickly gain access to its most critical parts. On the other hand, Linux users have lower access rights by default. In theory, this means that even if a virus does manage to penetrate the local files and folders, the core system remains safe and untouched.
By considering these points, it becomes evident why Linux is often viewed as a more secure option compared to other operating systems. Its open source nature, complex architecture and limited user rights contribute significantly to its robust defensive capabilities.
The Importance of Privacy and Anonsurf's Role
Why is privacy essential?
Privacy is the cornerstone of personal freedom. It might seem puzzling for some to comprehend why privacy is so crucial, particularly in the digital age. However, it boils down to one fundamental truth: without privacy, your ability to express yourself freely becomes limited. Money, whether it's in the form of traditional currency or cryptocurrencies like Bitcoin, is a potent form of expression. Each transaction you make represents a choice and can be seen as casting a vote.
When engaging with cryptocurrencies, many users prefer to maintain their anonymity for a multitude of reasons. Some may wish to transact without being subjected to scrutiny or surveillance, while others might simply want protection from potential hackers. Regardless of the reason, privacy remains an inherent human right that should be respected without requiring justification.
“Privacy is not about hiding something; it's about the ability to control what you reveal about yourself.”
The role of Anonsurf
Anonsurf is an open-source project that uses TOR iptables to anonymize your entire system thereby ensuring privacy during online interactions. It allows users full control over their network through the ability to start or stop the I2P project as needed. This enables users to experiment freely within Linux while running Anonsurf in the background.
For instance, you can run wallet apps, browsers, and other applications without leaving any traces of your actual IP address. The Anonsurf repository contains both Anonsurf and Pandora packages. Notably, Pandora overwrites RAM upon system shutdown and clears cache thus erasing all traces of user activity from the system. This function can be executed either automatically or manually.
What about VPNs?
At this point, you might wonder about VPNs (Virtual Private Networks). While VPNs offer a level of online privacy and security, they have their limitations. VPN service providers can potentially ‘read' your online activities. Even if you run a VPN over TOR, your privacy could still be compromised if any connection to your real identity is linked to the VPN provider.
“VPNs offer a level of privacy, but they are not foolproof. Your online activities can still be visible to the service provider.”
However, VPNs still have their place in the privacy landscape. They can serve as a powerful tool when used in conjunction with TOR, especially if you have managed to keep your real identity concealed online.
For more information on this, check out the Ultimate Guide to the Best VPN Services for Crypto Users.
Why Linux is more secure than other operating systems?
Linux is not just a random operating system, in fact, it's the world's most popular choice when it comes to servers, basically, our whole internet runs on Linux, while the average joe is still stuck with the Windows. We will not go too deep on describing why exactly Linux is considered far more secure than Windows or Mac. But here are a few obvious reasons.
To get started with this project, we suggest you obtain another laptop or pc which you can then play around in case something goes wrong. In practice, it also makes sense to have a separate machine that is specifically designed for handling cryptocurrencies only. After you get a hang of Linux, you may want to which it to your main operating system.
Embarking on Your Digital Security Journey
We recommend obtaining a separate laptop or PC. This not only acts as a safety net in case something goes wrong but also helps keep your digital currencies isolated from your everyday computer activities. As you get comfortable with Linux, you may even consider switching to it as your primary operating system.
To make this transformation smoother, follow these detailed steps:
Steps to Make Your Computer Ultra-Secure:
- Download the Ubuntu ISO file
- Create a bootable USB
- Boot from the USB
- Install Ubuntu
- Prepare Ubuntu
- Install Anonsurf
1. Download the Ubuntu ISO File
The first step is to download the original Ubuntu ISO file, which will serve as our operating system.
Navigate to the Ubuntu website and download the file. For this tutorial, we are using Ubuntu 18.04.3 LTS.
To ensure the authenticity and security of your download, we recommend verifying the file using this verification tutorial.
2. Create a Bootable USB
Next, you'll need a flash drive with at least 2GB of storage.
Format your flash drive to either FAT32 (for Windows users) or MS-DOS (FAT) (for Mac users).
Use tools like UNetBootin or Rufus to transform your formatted flash drive into a bootable device that can run Ubuntu.
There are numerous online tutorials available on how to do this. Simply search: “How to make a bootable Ubuntu flash drive.”
3. Boot from the USB
Now comes the exciting part! Insert your freshly minted bootable USB into your computer and restart it.
As your computer restarts, enter the BIOS settings (the key to press varies by manufacturer but is usually displayed during startup). Within the BIOS settings, navigate to the “Boot Order” section and select the USB drive option.
Once you've adjusted the boot order, save your changes and restart your computer. If done correctly, you will be greeted by the Ubuntu screen with two options: Try Ubuntu or Install Ubuntu. You can choose to explore Ubuntu without installing it by selecting Try Ubuntu, or dive right in by choosing Install Ubuntu.
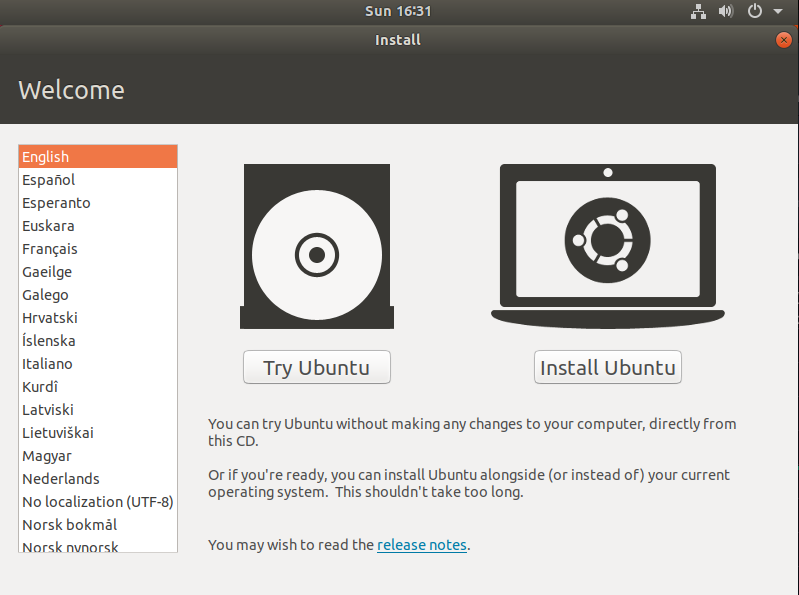
Proceed with Caution: Ensure you're utilizing a distinct hard drive or computer for this process.
Important Reminder: The safety and security of your computer and personal data are solely your responsibility!
Ubuntu Installation Process
1. Selecting the Appropriate Keyboard
The default keyboard layout is typically suitable for most users. However, you have the option to modify it according to your personal preference or specific regional requirements.
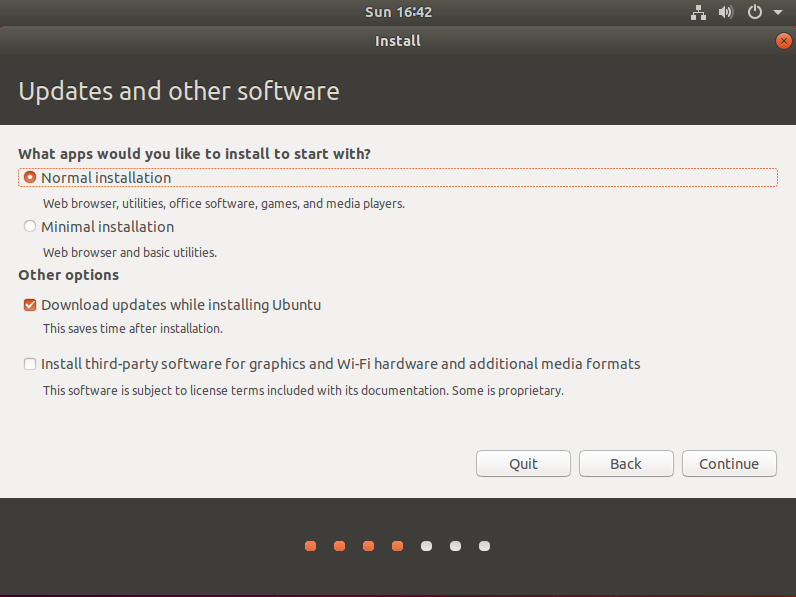
2. Selecting Installation Type and Software Updates.
Choose the ‘Normal installation' option, and ensure to check the box for ‘Download updates while installing Ubuntu'.
Please be aware that an active internet connection is required for this step.
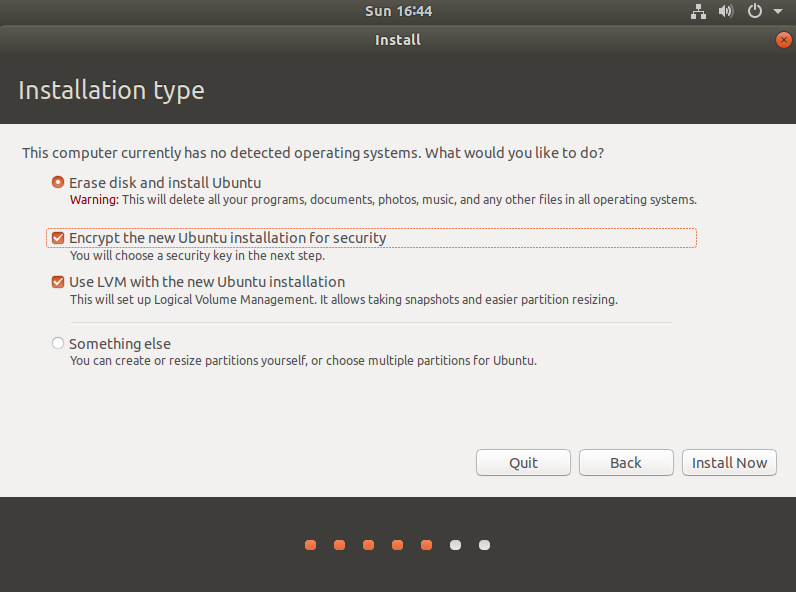
3. Choosing the Installation Type and Security Options
Opt for ‘Encrypt the new Ubuntu installation' to secure your system.
Ensure you select ‘Use LVM with the new Ubuntu installation' for enhanced management of your storage devices.
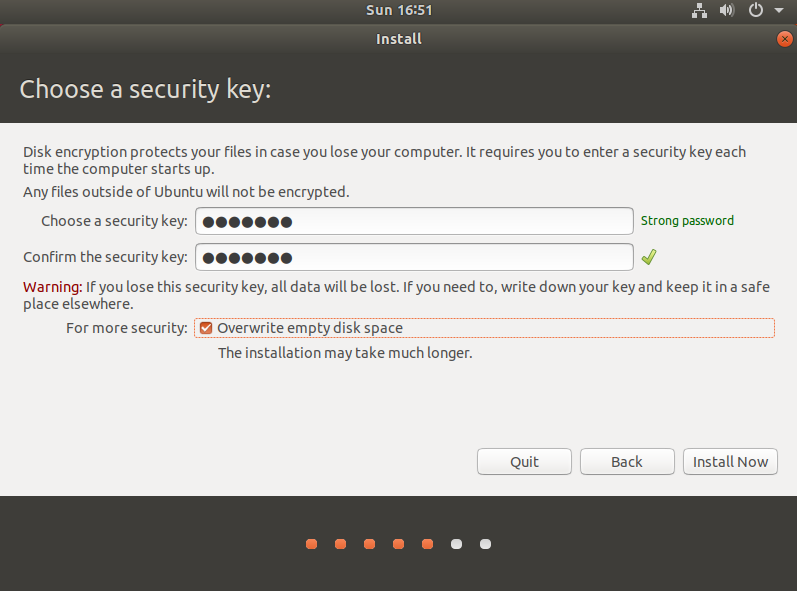
4. Establishing a Security Key
At this stage, you will configure your encryption key. This key serves as the gatekeeper to your hard drive – without it, no one can gain access. As such, ensure to jot it down in a secure location.
Additionally, make certain to select the “overwrite empty disk space” option. This is an integral component of the installation process.
Once completed, click on ‘Install Now'.
Did You Know?
The act of overwriting empty disk space is considered the most effective method of completely erasing a hard drive's data. (That is, unless you're inclined to use a power drill!)
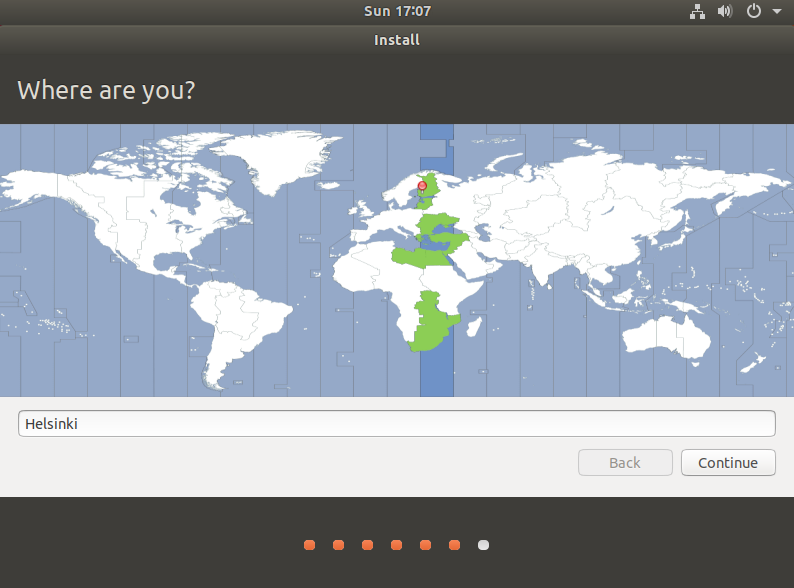
5. Setting Your Geographical Location:
Specify your country or regional area. This selection will define your time zone, currency, and numerical format (such as the use of periods or commas). It's pertinent to ensure accuracy for seamless system operations.
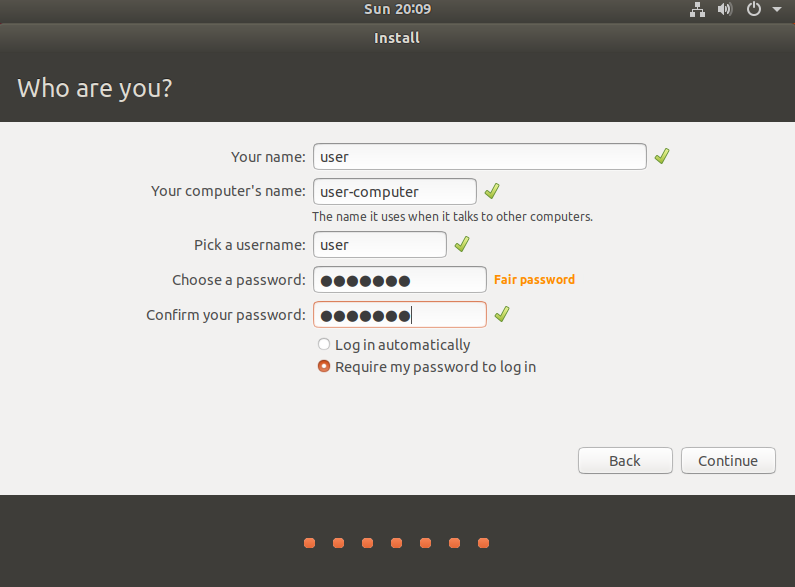
6. Creating Your Username and Password:
For this step, you will need to establish a unique username and password for your account. Remember, your selected password will also function as your sudo password, providing you with administrative permissions when necessary. It's critical to choose a strong and memorable password to maintain secure access to your system.
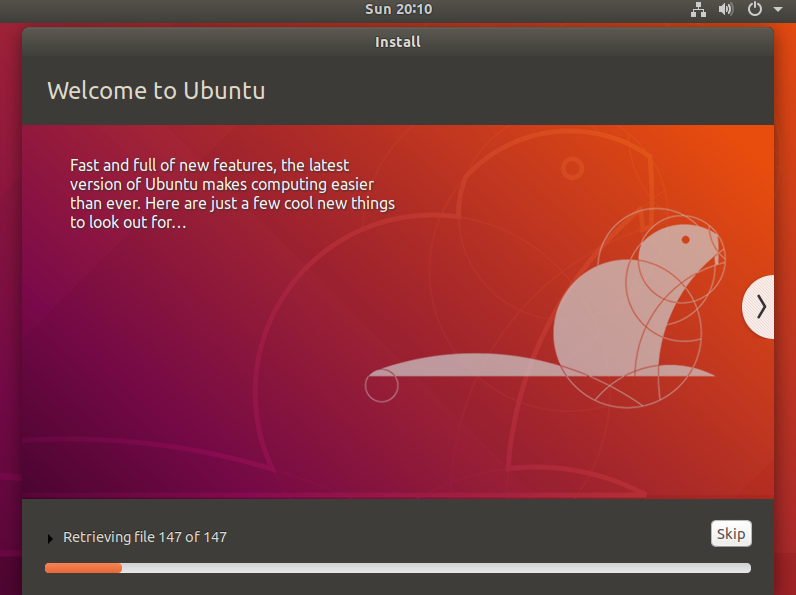
7. Executing the Installation Process
Allow the installation procedure to run its course to completion.
Conclusion
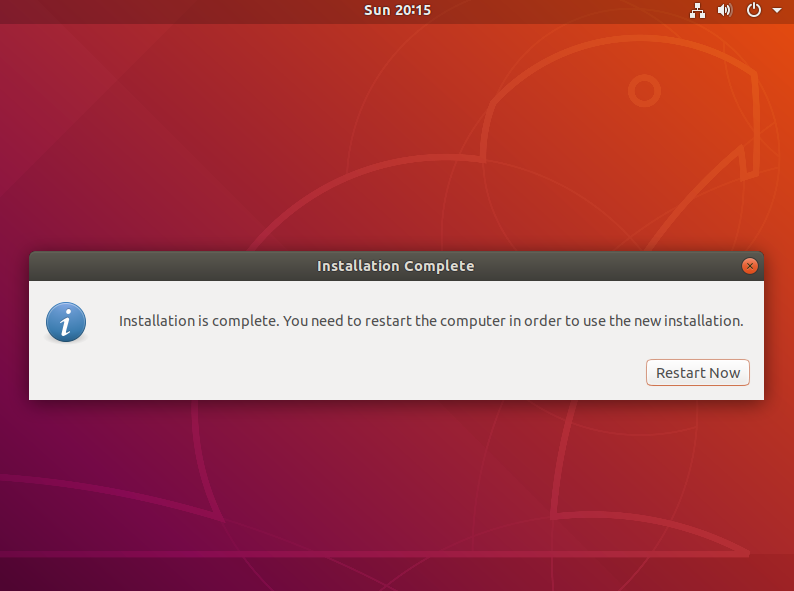
Upon completion, the system installer will display a dialog indicating Installation is Complete.
Proceed by clicking on ‘Restart Now', ensure to unplug your USB installation media, and allow your computer to reboot into Ubuntu.
Kudos! You've successfully installed a fully encrypted Ubuntu system. This high level of security ensures that it's virtually impossible for hackers to breach without your unique encryption key!
Getting Ubuntu Ready for Use
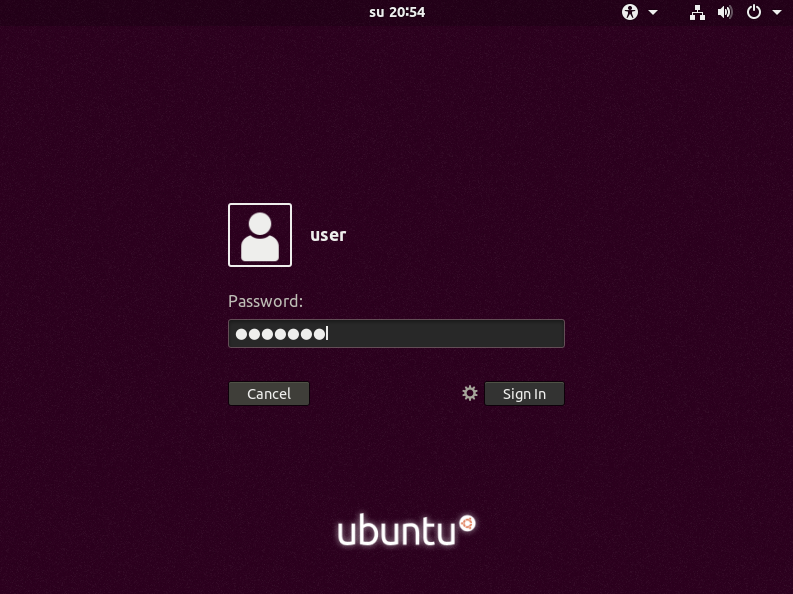
1. Initiating Disk Access
To initiate access to the system and its associated hard drive, it's mandatory to provide the designated encryption key.

2. Signing In
At this stage, you'll be prompted to select the user account that you've previously created.
Upon successful login, the following screen will be displayed.
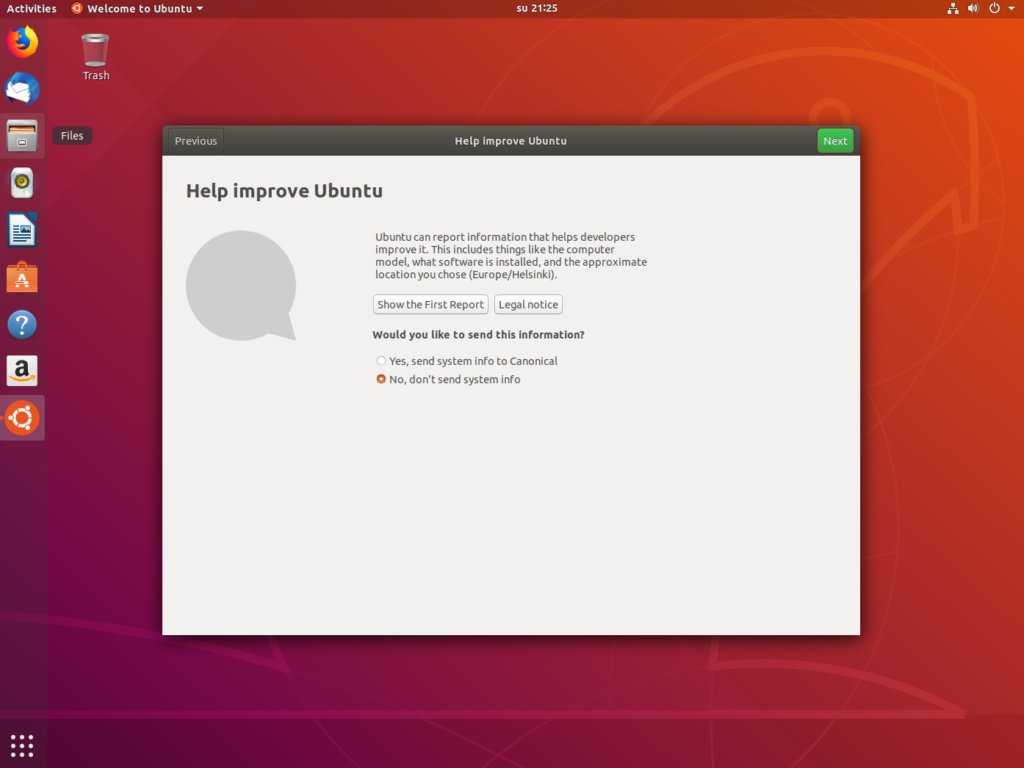
Proceed by clicking the ‘Next' button until you reach the section titled ‘Help Improve Ubuntu'.
Select the option ‘No, don't send system info', and conclude the introductory window by clicking ‘Next', followed by ‘Done'.
3. System Update
Once you've successfully logged in, your next task is to ensure that the system is up-to-date.
This can be achieved by executing the following commands:
sudo apt-get update
sudo apt-get upgrade
To get started, press: Ctrl + Windows key + T
This command will bring up a terminal window.
Alternatively, you can manually open a terminal by clicking on the “activities” tab found on the top left corner of the screen and typing: ‘terminal' into the search bar.
At this point, you'll need to input the following command: sudo apt-get update, and then press Enter.
You will be prompted for your user password. Carefully enter it and confirm by pressing Enter once more.
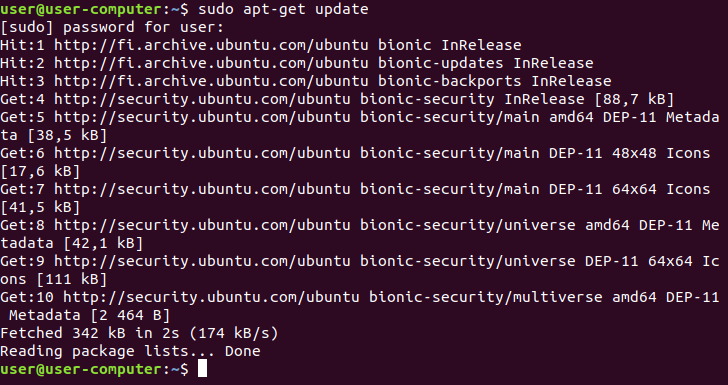
Once the package lists have been thoroughly read, input: sudo apt-get upgrade, and then press Enter.
Should a prompt appear asking “Do you want to continue?”, kindly respond by pressing Y, followed by Enter.
After ensuring your system is thoroughly updated, initiate a system restart by entering the command: ‘reboot', and pressing Enter.
Setting Up Anonsurf for Complete Anonymity
Having successfully updated our system, we'll now proceed to a thrilling segment of this tutorial – anonymizing the entire computer. Our strategy entails routing every single piece of network traffic through Tor. This not only guarantees an ultra-secure computer but also ensures complete anonymity.
The tool that makes all this possible is anonsurf, a program specifically designed for this purpose.
Here's the Github link: https://github.com/Und3rf10w/kali-anonsurf
We will be using the following commands:
- Install git:
sudo apt-get install git - Clone the Anonsurf repository:
git clone https://github.com/Und3rf10w/kali-anonsurf - Change directory to the cloned repository:
cd kali-anonsurf/ - Install Anonsurf:
sudo ./installer.sh
To get started, open a terminal window using Ctrl + Windows key + T, just like we did earlier.
Type: sudo apt-install git
The system will ask for confirmation; press Y to continue.
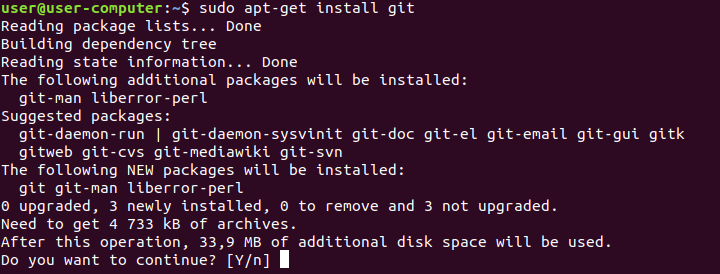
Once the installation is complete, execute the following command: git clone https://github.com/Und3rf10w/kali-anonsurf“.
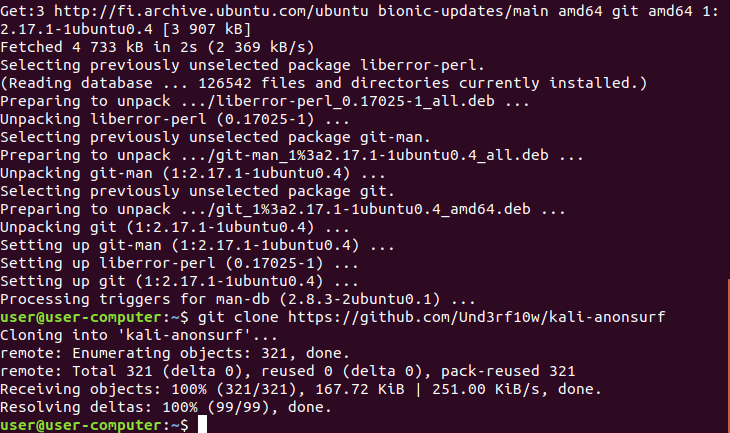
Navigate to the cloned repository by executing the command: cd kali-anonsurf/
This command will shift the current folder directory to kali-anonsurf.
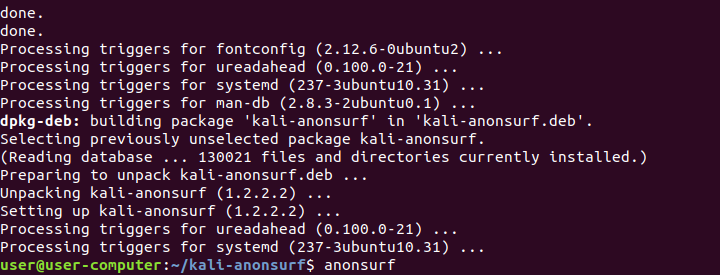
To initiate Anonsurf installation, input: sudo ./installer.sh
Upon successful completion of the installation, enter the following command: anonsurf.
Proceed by entering the following command: sudo anonsurf start”.
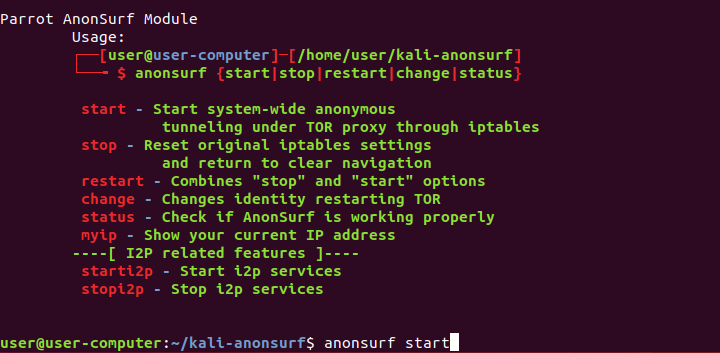
Voila!
Your entire system is now configured to route all network traffic via Tor.
You are fully cloaked in anonymity!
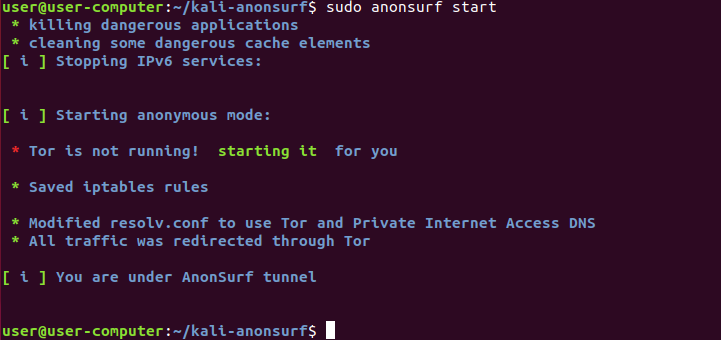
To verify the effectiveness of your new setup, you can immediately conduct a quick test. Simply launch Firefox, enter “what is my ip” into the search bar of DuckDuckGo, and execute the search.
You can leverage websites that display your external IP such as www.ipleak.net to verify if Anonsurf is functioning correctly.
In some cases, the connection may not pick immediately after starting Anonsurf. If you encounter this issue, try stopping it by typing sudo anonsurf stop. Afterward, check if you can connect normally to the internet. If successful, attempt starting Anonsurf again and see if it works.
Alternatively, the command sudo anonsurf restart can also be used to restart Anonsurf.
To change your Tor identity at any time, use the command: sudo anonsurf change.
For a list of other useful commands, simply type anonsurf into a terminal.
Please note that Anonsurf must always be used under Root privileges. This means you will need to type “sudo” and enter your password whenever changing your network settings.
With these steps completed, your computer is now one of the most ultra-secure machines available.
Conclusion
Congratulations! You've now transformed your computer into one of the most secure machines available. This is particularly beneficial when dealing with sensitive transactions, such as those in the ever-evolving sphere of cryptocurrency.
However, it's important to remember that cybersecurity is a journey, not a destination. Never rest on your laurels. The landscape of security in the realm of cryptocurrency is vast and continuously evolving. Hence, there's always more to learn to keep up with the latest security trends and techniques.
Expand Your Knowledge
Consider delving into other pertinent topics such as:
- Securing your Wallets: It's not enough to have a secure machine; you need to ensure that your digital wallets are secure too. Explore different ways to enhance wallet security like multi-factor authentication, encryption, hardware wallets, and more.
- Employing VPNs with TOR: While TOR provides anonymity, using a Virtual Private Network (VPN) can add an extra layer of security by encrypting your internet traffic and hiding your IP address. Learn how to use them in conjunction for maximum protection.
- Understanding Non-KYC Exchanges: Know Your Customer (KYC) norms can sometimes compromise privacy while trading cryptocurrencies. Non-KYC exchanges provide an alternative for those seeking privacy but understanding their risks and benefits is crucial.
- Exploring More about Anonsurf Commands: Anonsurf has many other commands besides
start,stop, andchange. Each offers unique functionalities that could be useful in different scenarios.
Remember,
“The only system which is truly secure is one which is switched off and unplugged, locked in a titanium lined safe, buried in a concrete bunker, and is surrounded by nerve gas and very highly paid armed guards.” – Gene Spafford
While achieving absolute security might be a utopian ideal, improving your knowledge about cybersecurity can help you make savvy decisions and reduce risks significantly. So continue learning, exploring, and enhancing your security prowess.
FAQs (Frequently Asked Questions)
What are the defining aspects of Linux?
First and foremost, one of the defining aspects of Linux is its open-source nature.
How does the architecture of Linux differ from Windows?
Unlike Windows, which has a relatively straightforward structure, Linux has a complex architecture.
What is the role of Anonsurf in enhancing privacy?
Anonsurf is an open-source project that uses TOR iptables to provide complete anonymity and enhance privacy.
Why is privacy essential?
Privacy is the cornerstone of personal freedom. It is essential for maintaining autonomy and security in the digital age.



